Developer Offer
Try ImaginePro API with 50 Free Credits
Build and ship AI-powered visuals with Midjourney, Flux, and more — free credits refresh every month.
Chinese Hackers Weaponize ChatGPT for Advanced Cyberattacks
The Rise of AI-Powered Cyberattacks
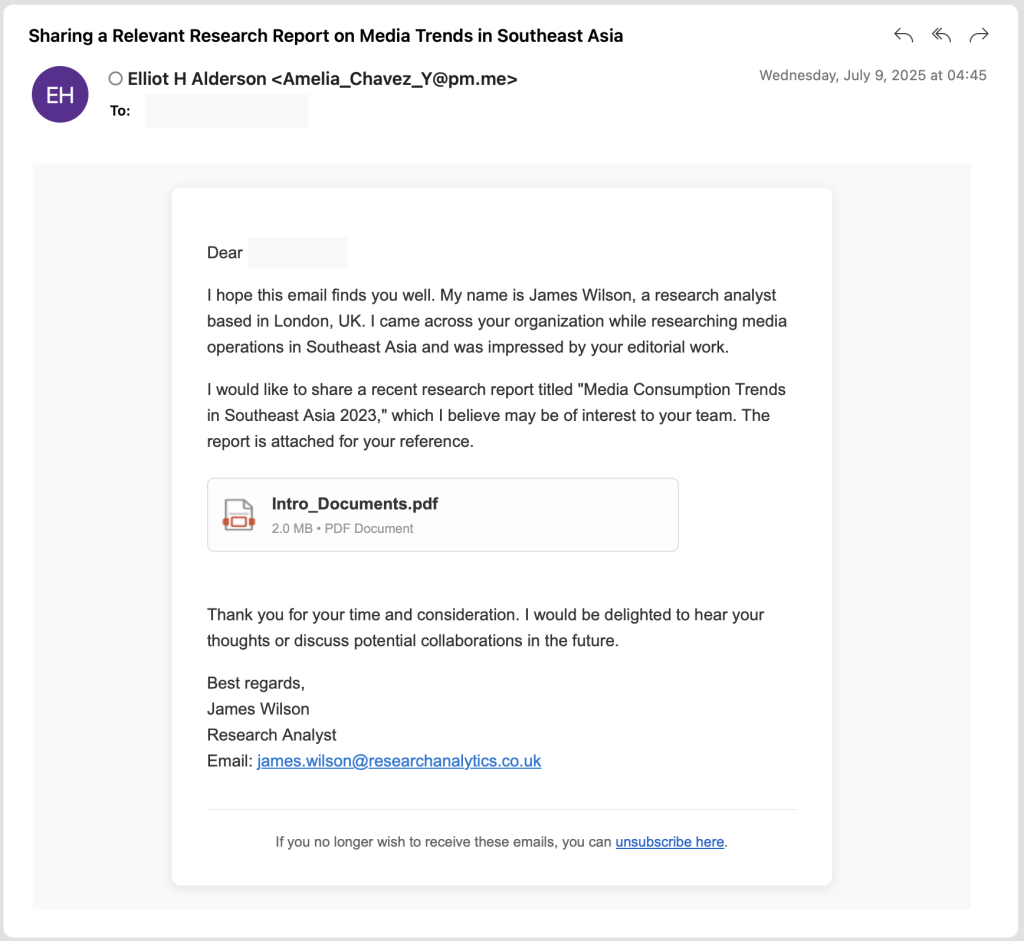
Security researchers at Volexity have uncovered alarming evidence of China-aligned threat actors weaponizing artificial intelligence platforms like ChatGPT to dramatically upgrade their cyberattack capabilities. A group tracked as UTA0388 has been conducting advanced spear phishing campaigns since June 2025, using AI to develop sophisticated malware and craft convincing phishing emails in multiple languages.
These campaigns, targeting organizations across North America, Asia, and Europe, display an unprecedented level of sophistication. By leveraging Large Language Models (LLMs), UTA0388 automates the creation of fabricated personas and fictional research organizations to socially engineer their targets into downloading malicious payloads.
The sheer volume and linguistic diversity of the attacks—spanning English, Chinese, Japanese, French, and German—far surpass what is possible through traditional, human-led operations. Researchers observed over 50 unique phishing emails that were fluent but often semantically incoherent, such as an English email body with a Mandarin subject line. This incongruity strongly points to AI generation. The group also employs a "rapport-building phishing" strategy, where initial emails are benign to establish trust before a malicious link or file is sent, minimizing their operational exposure.
Dissecting the GOVERSHELL AI-Generated Malware
A deep technical analysis, detailed in a Volexity report, reveals five distinct variants of a custom malware dubbed GOVERSHELL. The fact that each variant is a complete rewrite, rather than an iterative update, suggests the use of AI for rapid code generation.
These variants utilize diverse command-and-control (C2) mechanisms, from fake TLS communications to WebSocket connections, with rewritten network stacks in each version. For persistence on an infected system, the malware uses scheduled tasks and search order hijacking techniques, which involve loading malicious DLLs alongside legitimate programs.
Further evidence includes developer paths containing Simplified Chinese characters and metadata indicating the use of python-docx, a library frequently employed by LLMs for document generation. OpenAI's own October 2025 report confirmed UTA0388's use of ChatGPT for these activities, noting the presence of odd "Easter eggs" like pornographic content and Buddhist recordings within malware archives, likely a result of the AI's lack of contextual awareness.
A New Era of Cyber Threats and How to Defend Against It
The integration of AI into cybercrime signals a new era of automated and large-scale threats. Traditional defenses that rely on spotting linguistic errors in phishing emails may no longer be effective against fluent, AI-generated content.
To counter this evolving threat, organizations must enhance their security posture:
- Augment Email Security: Implement behavior-based detection to monitor for anomalies like the reply-chain tactics used in rapport-building phishing.
- Strengthen Endpoint Security: Deploy solutions capable of detecting unusual persistence mechanisms like search order hijacking.
- Prioritize Threat Intelligence: Sharing indicators of compromise (IOCs) for threats like GOVERSHELL is crucial for community-wide defense.
- Patch Vigilantly: Regularly update systems to patch known vulnerabilities that are often exploited through malicious documents.
As threat actors evolve, so too must our defenses. Adopting AI-driven security analysis and anomaly detection is essential to effectively counter these next-generation threats.
Key Vulnerabilities Exploited
| CVE ID | Description | Impact | CVSS 3.1 Score |
|---|---|---|---|
| CVE-2022-30190 | Microsoft Follina: RCE via malicious Word documents | Remote code execution | 7.8 |
| CVE-2023-23397 | Microsoft Outlook elevation of privilege | Credential theft / code execution | 9.8 |
| CVE-2023-21803 | Microsoft Visio RCE via crafted VSDX files | Remote code execution | 8.6 |
Compare Plans & Pricing
Find the plan that matches your workload and unlock full access to ImaginePro.
| Plan | Price | Highlights |
|---|---|---|
| Standard | $8 / month |
|
| Premium | $20 / month |
|
Need custom terms? Talk to us to tailor credits, rate limits, or deployment options.
View All Pricing Details